Specify relative time ranges.
Splunk specify time range in query.
In general you won t specify latest without an earliest time.
When you add data to the splunk platform the data is indexed.
To search for the terms error fail failure failed or severe in the events that also mention buttercupgames run the following search.
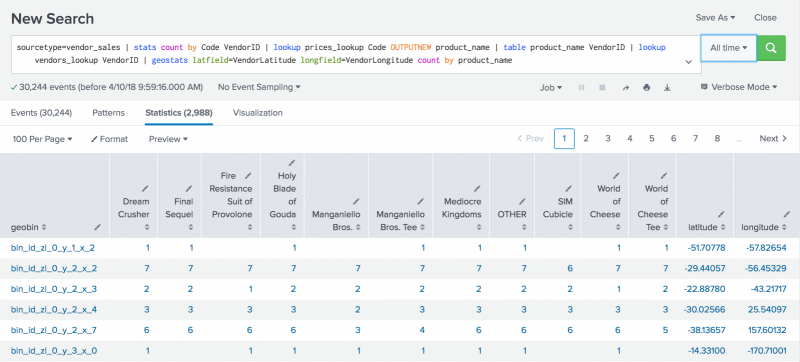
The patterns tab displays a list of the most common patterns among the set of events returned by your.
You can use the relative option to specify a custom time range.
Open the time range picker.
Hello splunkers i have an iis log that i am testing against and i have a need to test for a specified range the time field in the log is formatted like this 2020 08 23t21 25 33 437 0400 2020 08 23t21 25 33 437 0400 i want to query everything between 21 25 33 and 21 25 43 2020 08 23t21 25 33 437.
I have tried setting the earliest latest variables e g earliest 1 latest now but this only seems to work on events that fall within the bounds of the time range picker.
When you specify a time range in your search or saved search it overrides the time range that is selected in the dropdown menu.
The time field in the log is formatted like this 2020 08 23t21 25 33 437 0400.
However the time range specified directly in the search string will not apply to subsearches but the dropdown selected range will apply.
For example if you specify a time range of last 24 hours in the time range picker and in the search bar you specify earliest 30m latest now the search only looks at events that have a timestamp within.
I have an iis log that i am testing against and i have a need to test for a specified range.
A time range that you specify in the search bar or in a saved search overrides the time range that is selected in the time range picker.
Custom logic for dashboards.
If you do not specify a time offset before the snap to amount splunk software interprets the time as current time snapped to the specified amount.
Specify specific time range in query irishmanjb.
This feature is accessed through the app named as search reporting which can be seen in the left side bar after logging in to the web interface.
The number of events returned should be larger.
Splunk has a robust search functionality which enables you to search the entire data set that is ingested.
On clicking on the search reporting app we are presented with a search box where we can start our search on the log data that we uploaded.
Use a custom time range when one of the preset time ranges is not precise enough for your search.
Path finder a month ago hello splunkers.
For example if it is currently 11 59 pm on friday and you use w6 to snap to saturday the resulting time is the previous saturday at 12 01 a m.
You changed the time range from last 24 hours to yesterday.
For both condition and eval elements all data available from an event as well as the submitted token model is available as a variable within the eval expression.
I am trying to understand time is recognized by splunk or not.
Change the time range to all time.
Meaning if i have my time range picker set for the last 30 days then the earliest and latest will only return events that fall within both the last 30 days and.